Exam Topics
- F5CAB1
- F5CAB1.01
- Securing Management-IP
- SSHD ACLs
- HTTPd ACLs
- F5CAB1.01
SSHd and HTTPd ACLs
Securing management access to the BIG-IP is critical for maintaining a secure and stable environment. You can harden access through the Self-IP using the Port Lockdown feature in a restrictive mode. However, Port Lockdown alone is not enough for complete control. In this article, we will explore another way to strengthen management access for SSH and HTTP using daemon ACLs.
What are HTTPd and SSHd Daemons in F5 Big IP ?
- HTTPd (HTTP Daemon): This is the process that runs the BIG-IP Configuration Utility, the web-based management interface. When you connect to BIG-IP via a browser using HTTPS, you are interacting with the httpd daemon. It allows administrators to manage virtual servers, pools, security policies, and more through a graphical interface.
- SSHd (Secure Shell Daemon): This daemon enables command-line management over SSH. It provides secure, encrypted remote access to the BIG-IP system for advanced configuration, troubleshooting, and automation tasks. SSH is essential for administrators who manage the system via CLI instead of the web UI.
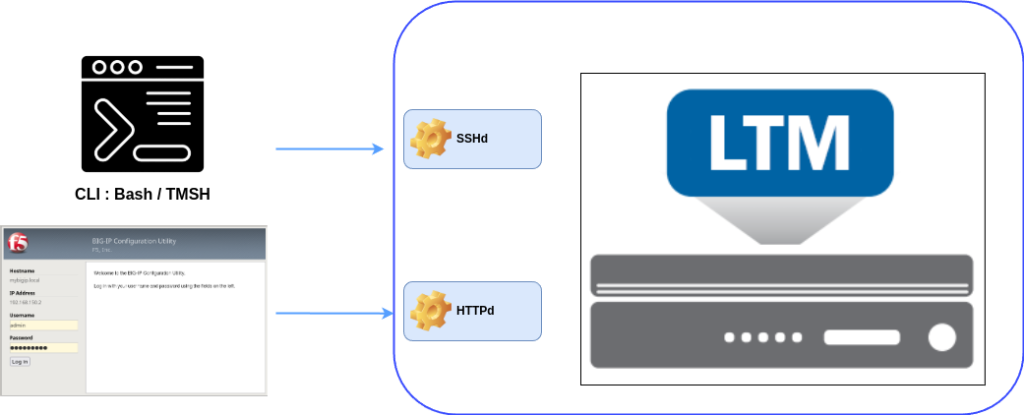
Both daemons are critical for system management, but they also represent potential attack vectors if left exposed to unauthorized users.
Port Lockdown or HTTPd/SSHd ACLs ?
While Port Lockdown restricts access to entire services (for example, SSH or HTTP) on a Self-IP, daemon ACLs offer more granular control, allowing you to define who can access these services. With ACLs, you can specify allowed hosts, IP ranges, or network prefixes that are permitted to connect. This applies to both Self-IP addresses and the Management IP address, providing an extra layer of security beyond the firewall.
Why restrict access of the SSH and HTTP daemon ?
It is essential to allow management access only to authorized administrators. Consider your corporate network, which includes both regular users and administrators. Without SSHd and HTTPd ACLs:
- Any internal user could attempt to access management services. For instance, a sales agent or HR employee has no need to view the Configuration Utility. If they gained access—intentionally or accidentally—they could cause catastrophic configuration changes.
- Guest network users could launch attacks. Imagine your company hosts a guest Wi-Fi network. A malicious guest could try to access the Configuration Utility and perform brute-force attacks to gain control of the BIG-IP system.
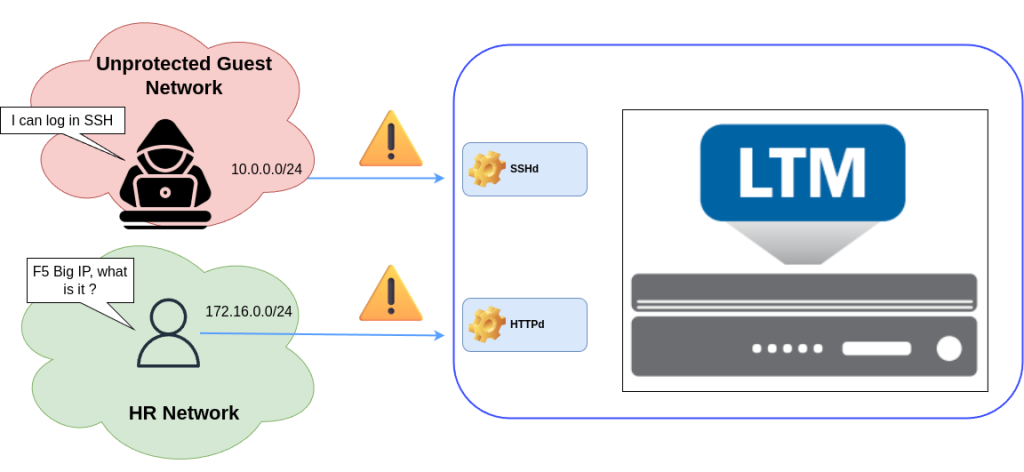
Even if you have internal firewalls in place, relying solely on them is not sufficient. Defense in depth is a security best practice. By implementing SSHd and HTTPd ACLs, you explicitly whitelist the devices or networks that can access management services, reducing the attack surface significantly.
How to configure Daemon ACLs on F5 ?
Configure SSHd ACL using the Configuration Utility
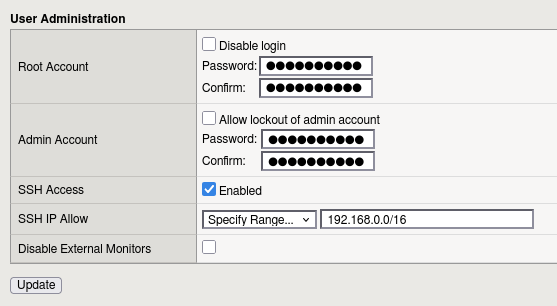
To be straightforward, you can configure which hosts and networks are allowed to access the SSH daemon (command-line interface) directly from the System → Platform page in the BIG-IP GUI.
The SSH IP Allow option lets you specify individual hosts or entire networks that are permitted to connect to the SSH daemon.
Configure SSHd ACL using TMSH
The SSHd ACL configuration is stored in the file /etc/hosts.allow.
[root@mybigip:Active:Standalone] config # cat /etc/hosts.allow
#
# THIS IS AN AUTO-GENERATED FILE - DO NOT EDIT!!!
#
# Use the tmsh shell utility to make changes to the system configuration.
# For more information, see tmsh -a help sys global-settings.
#
# hosts.allow This file describes the names of the hosts which are
# allowed to use the local INET services, as decided
# by the '/usr/sbin/tcpd' server.
#
# You MUST always allow ssh access for the 127. network
sshd : 127. : spawn (/usr/bin/autohost.sh %a)
in.tftpd : 127.
sshd : 192.168.0.0/255.255.0.0
big3d : ALL
snmpd : 127.0.0.0/255.0.0.0
You can view the line that control SSHd access in this file to see which hosts or networks are currently allowed. In this case the 192.168.0.0/16 network.
You can use tmsh to modify the list of allowed hosts for the SSH daemon.
Syntax
modify /sys sshd allow [add | delete | none | replace-all-with] { network }
Example
To allow only the network 192.168.0.0/16 to access SSH:
modify /sys sshd allow replace-all-with { 192.168.0.0/16 }
Verify the configuration
You can check that the new network is correctly applied by viewing the auto-generated /etc/hosts.allow file:
[root@mybigip:Active:Standalone] config # cat /etc/hosts.allow
... Omitted ...
sshd : 192.168.0.0/255.255.0.0
Configure HTTPd ACL
While the SSHd ACL can be configured using either tmsh or the Configuration Utility, the HTTPd ACL—which controls access to the web-based Configuration Utility—can only be configured using tmsh.
Syntax
modify /sys httpd allow [add | delete | none | replace-all-with] { network }
Example
To allow only the network 192.168.0.0/16 to access the Configuration Utility:
modify /sys httpd allow replace-all-with { 192.168.0.0/16 }
Using add, both 192.168.0.0/16 and ALL are allowed. This add 192.168.0.0/16 to the list but doesn’t remove the default ALL statement. This can create a false security sentiment because all host can still connect to the Configuration Utility :
root@(mybigip)(cfg-sync Standalone)(Active)(/Common)(tmos)# modify /sys httpd allow add { 192.168.0.0/16 }
root@(mybigip)(cfg-sync Standalone)(Active)(/Common)(tmos)# list /sys httpd allow
sys httpd {
allow { ALL 192.168.0.0/16 }
}
Use replace-all-with to only configure the 192.168.0.0/16 network (or alternatively remove ALL using delete).
Summary
Properly securing BIG-IP Configuration Utility and SSH access is essential to protect your system from unauthorized users. While Port Lockdown restricts access broadly, SSHd and HTTPd ACLs provide fine-grained control, letting you specify exactly which hosts or networks can access SSH and the Configuration Utility.
By configuring ACLs correctly, you can :
- Ensure that only authorized hosts can access the Configuration Utility and SSH.
- Reduce the risk of accidental or malicious changes.
- Strengthen your overall security posture and enforce defense-in-depth.
Now that you’ve learned about daemons ACL, why don’t you explore the other topics in the F5CAB1 blueprint ?