Exam Topics
- F5CAB1
- F5CAB1.01
- Port lockdown
- F5CAB1.02
- Interpret port lockdown settings to Self-IP
- F5CAB1.01
- F5CAB4
- F5CAB4.02
- Interpret port lockdown settings to Self-IP
- F5CAB4.02
Introduction
On F5 BIG-IP, the Port Lockdown feature is used to define which protocols and ports are allowed for incoming connections to a Self-IP address. If a protocol or port is not included in the Port Lockdown list, any connection attempt to the Self-IP on that port will be rejected. Outbound connections are not restricted by Port Lockdown, so services like health monitors or connections to backend servers do not need to be explicitly allowed in the Port Lockdown list.
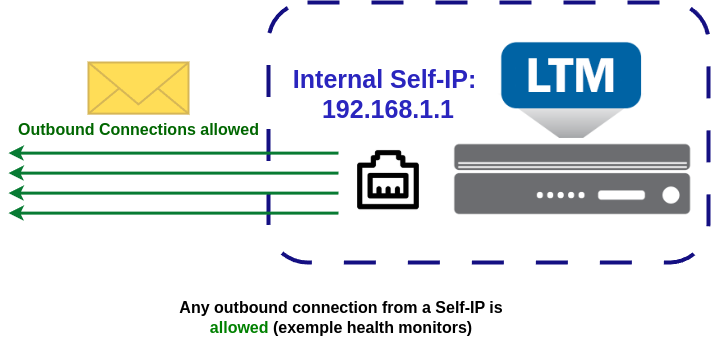
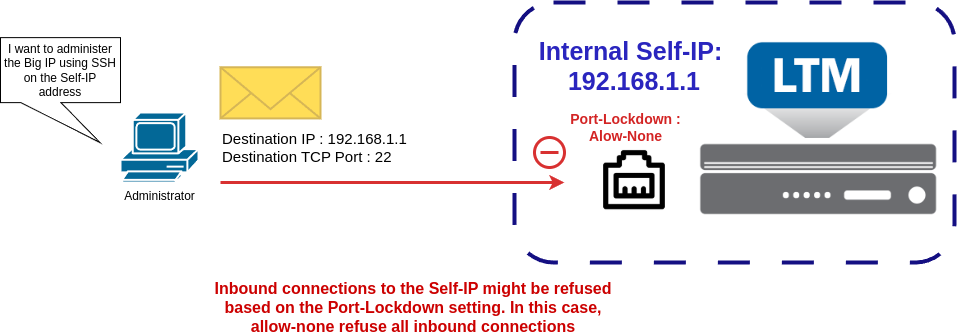
While outbound connections are always allowed, inbound connections can be blocked by Port Lockdown. By default, when a Self-IP is created, the Port Lockdown mode is set to Allow None, which means all inbound connections are rejected. As a result, an administrator cannot access the BIG-IP via the Self-IP until the Port Lockdown settings are modified to permit the required protocols or ports.
Port Lockdown Modes on a Self-IP
On a Self-IP, you can configure the following Port Lockdown modes:
- Allow-None
- This is the default setting when creating a Self-IP. It denies all inbound traffic, except exceptions.
- Allow Default
-
- Allows a predefined set of ports and services commonly used for BIG-IP management and control traffic.
Protocol Port/Service Description IGMP Not applicable Multicast group management OSPF Not applicable Routing protocol PIM Not applicable Multicast routing TCP 4353 iQuery UDP 4353 iQuery TCP 443 HTTPS (Configuration Utility) TCP 161 SNMP UDP 161 SNMP TCP 22 SSH TCP 53 DNS UDP 53 DNS UDP 520 RIP UDP 1026 Network Failover -
- Allow Custom
- Allows you to manually define the protocols and ports for which inbound connections are permitted on the Self-IP.
- Allow Custom (Include Default)
- Allows the default list of services (from Allow Default) plus any additional services you configure.
- Allow All
- Allows all incoming connections to the Self-IP on all ports.
Why restrict access to Self-IP using Port-Lockdown ?
From a security perspective, it is important to allow only the services that are strictly necessary on a Self-IP. Consider the following architecture: a BIG-IP device with both external and internal Self-IPs.
-
External Self-IP: Users connect to virtual servers through this address.
-
Internal Self-IP: Used for connections initiated by the BIG-IP itself, such as backend server communication.
If the external Self-IP is configured with a permissive Port Lockdown setting, such as Allow Default, it could pose a security risk. For example, administrative services like SSH or the configuration utility could inadvertently be exposed to the internet, creating potential attack vectors.
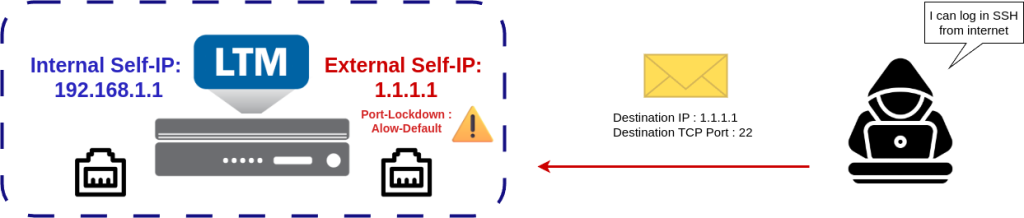
For improved security, it is recommended to set Port Lockdown to Allow None on external Self-IPs. This ensures that no unnecessary services are exposed to external networks. For internal Self-IPs, use the Custom option to allow only the specific services that are required (such as SSH or HTTPS for management). Avoid relying on Allow Default, as it permits a broad range of services that may not all be needed in your environment.
Port-Lockdown exceptions
Some traffic is always allowed on a Self-IP, regardless of the Port Lockdown mode—even if it’s set to Allow None. These exceptions include:
| Service | Protocol / Port Range | Applies To | Description |
|---|---|---|---|
| TCP Mirroring | TCP / 1029–1155 | Self-IP where TCP Mirroring is enabled | Used by the connection mirroring feature to replicate state information between BIG-IP devices in a cluster. |
| Centralized Management Infrastructure (CMI) | TCP / 4353 | Self-IP where CMI is enabled | Used for device-to-device communication when BIG-IP devices are part of a synchronization group. |
| ICMP | ICMP | All Self-IPs | Internet Control Message Protocol is always enabled and is not affected by the Port Lockdown configuration. |
| Virtual Server | Protocol/Port of the Virtual Server | Self-IP where the Virtual Server is configured | When a Virtual Server is configured on a Self-IP, it overrides the Port Lockdown setting for that specific protocol and port. |
For example, if an HTTP Virtual Server is configured to listen on Self-IP A, that Self-IP will automatically allow inbound connections on port 80. Without this exception, you would need to manually add every protocol and port used by virtual servers to the Port Lockdown list.
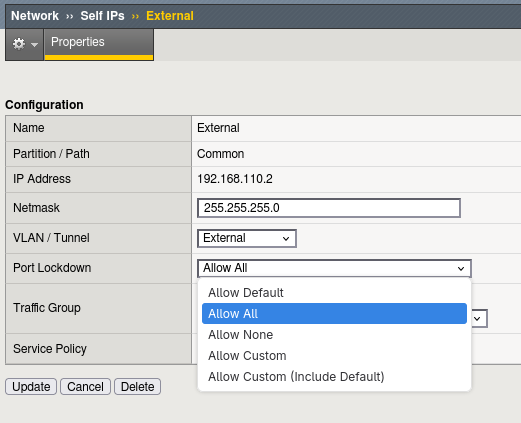
Configuring port-lockdown using the Configuration Utility
Access the Self-IP configuration using Network->Self-IPs.
In the self-IP configuration menu, you can select the Port-Lockdown setting needed (Allow-None, Allow-Default, Allow-Custom, Allow-All)
Configuring port-lock using tmsh
You can modify the Port Lockdown setting of a Self-IP using the following syntax:
modify /net self <Self-IP-Name> allow-service { all | default | none }
You should replace <Self-IP-Name> with the name of the Self-IP configured on your BIG-IP, and choose the allow-service option that fits your needs.
For example, to set Port Lockdown to allow-default on an External Self-IP, the command would be:
modify /net self External allow-service default
You can verify the Port Lockdown configuration for a specific Self-IP using the following command:
list /net self <Self-IP-Name> allow-service
Summary
-
Port Lockdown limits access to a Self-IP, securing inbound connections.
-
The default Port Lockdown setting is Allow None, which denies all inbound connections.
-
The Port Lockdown modes are:
-
Allow None
-
Allow Default
-
Allow Custom
-
Allow Custom (Include Default)
-
Allow All
-
-
Certain traffic always bypasses Port Lockdown, including virtual server service ports, ICMP, TCP Mirroring, and CMI.
-
Port Lockdown is configured in the Network → Self-IP configuration menu.
Now that you’ve learned about Port Lockdown, explore the other topics in the F5CAB1 blueprint to continue your BIG-IP journey.”