Exam Topics
- F5CAB1
- F5CAB1.01
- Configure DDoS Vectors
- F5CAB1.01
Introduction
Distributed Denial of Service (DDoS) attacks aim to disrupt services by overwhelming systems with excessive traffic or resource consumption. To mitigate them effectively, it is essential to understand the different DDoS attack types and how they are detected and handled.
This article begins with a brief overview of DDoS attacks and the four main DDoS vectors, explaining why mitigation is critical for service availability.
It then explores how F5 AFM detects and mitigates DDoS attacks using detection and mitigation thresholds.
You will also learn how these thresholds can be configured, either manually or automatically, and how to apply DDoS protection using the BIG-IP Configuration Utility.
By the end of this article, you will have a clear understanding of how DDoS vectors are handled on F5 AFM and how to configure effective mitigation.
Distributed Denial of Service (DDoS) Attacks
A Denial of Service (DoS) or Distributed Denial of Service (DDoS) attack is designed to make a service unavailable to legitimate users. While a DoS attack typically originates from a single source, a DDoS attack is launched from multiple distributed systems, often part of a botnet, making it far more difficult to detect and mitigate.
The primary objective of these attacks is not to breach security, but to exhaust resources such as bandwidth, CPU, memory, or connection tables, until the targeted service can no longer respond correctly.
Common Symptoms of DDoS Attacks
DoS and DDoS attacks can manifest in several ways, depending on the targeted resources and attack type. Common symptoms include:
- Slow network performance, with increased latency and packet loss
- Intermittent or complete inability to access a website or application
- Long response times or frequent connection timeouts
- Service instability, where applications crash or restart unexpectedly
- Prolonged denial of access to web services or even all Internet connectivity in severe cases
The consequences of a successful DoS or DDoS attack can be significant. Beyond immediate service disruption, organizations may face revenue loss, reputation damage, breach of service-level agreements, and increased operational costs.
Types of Dos and DDoS Attacks
DDoS attacks can be broadly classified into four main categories, based on the resources they target and the techniques they use.
1. Volumetric Attacks
Volumetric attacks aim to saturate network bandwidth by generating massive amounts of traffic. These are flood-based attacks that overwhelm links, routers, or load balancers before the traffic even reaches the application.
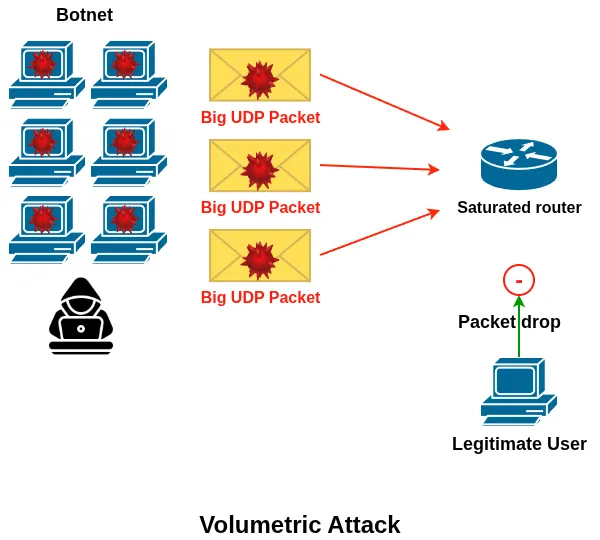
Common examples include UDP floods, ICMP floods, and amplification attacks.
The goal is simple: consume all available bandwidth so legitimate traffic cannot pass.
2. Computational Asymmetric Attacks
Computational asymmetric attacks are designed to consume excessive CPU resources on the target system. They exploit operations that are cheap for the attacker to generate but expensive for the server to process.
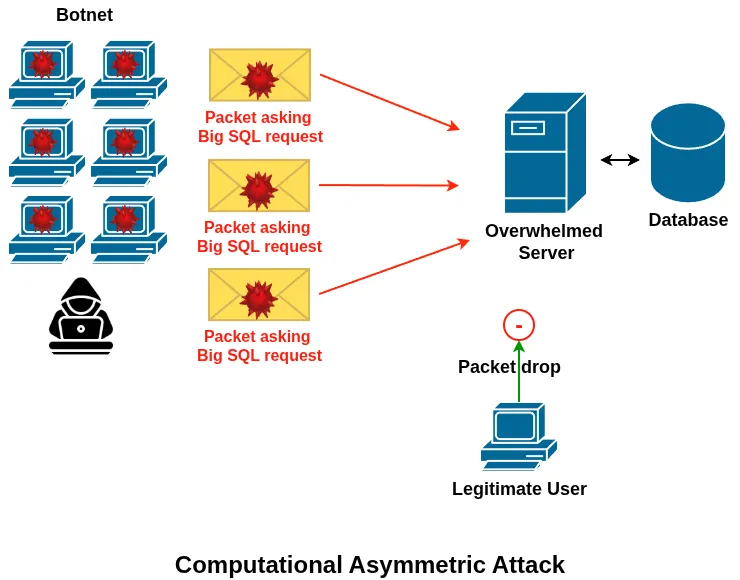
Examples include SSL handshake floods or malformed requests that trigger costly processing. Even a relatively low traffic rate can have a severe impact if each request requires significant CPU cycles.
3. Stateful Asymmetric Attacks
Stateful asymmetric attacks target memory and state tables by abusing session handling and timeouts. These attacks create large numbers of half-open or long-lived connections, forcing the system to allocate and maintain state information.
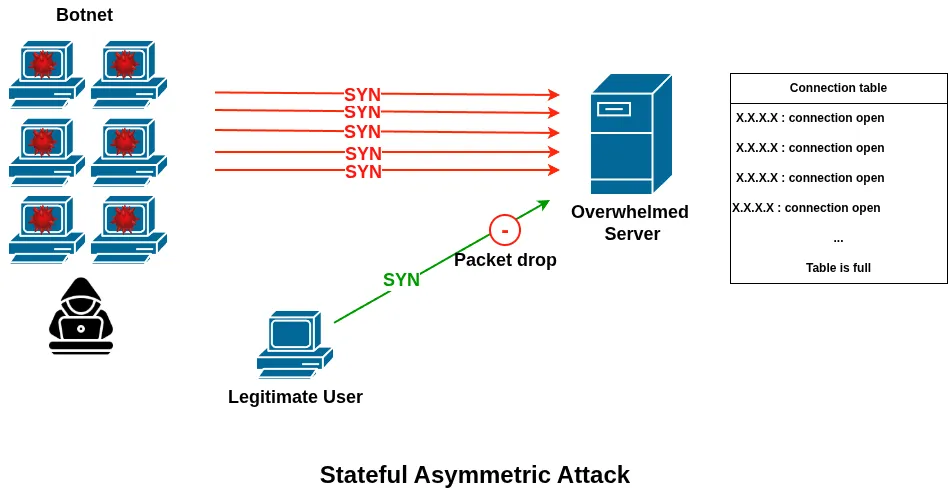
Over time, this exhausts memory and connection tables, preventing new legitimate sessions from being established. SYN floods are a classic example of this attack category.
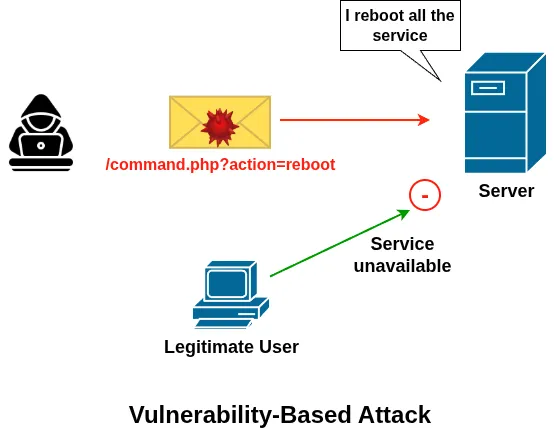
4. Vulnerability-Based Attacks
Vulnerability-based attacks exploit software weaknesses or protocol flaws at any layer of the stack. Instead of overwhelming resources through volume, these attacks trigger bugs or unexpected behavior that can crash services or degrade performance.
Because they rely on specific vulnerabilities, these attacks can be highly effective even with minimal traffic and may bypass traditional rate-based protections if not properly detected.
Configure DDoS Vectors Using the F5 AFM Configuration Utility
Now that we have reviewed the four common DDoS attack categories and how they impact application stability, let’s look at how to defend against them using F5 AFM.
To provide DDoS protection, the AFM module introduces the concept of DDoS vectors. A DDoS vector represents a specific attack type and groups similar attack behaviors into categories. AFM provides DDoS vectors for three main protocol families:
-
Network
-
DNS
-
SIP
Depending on the BIG-IP version, AFM includes severals individual DDoS vectors, each designed to detect and mitigate a specific type of attack.
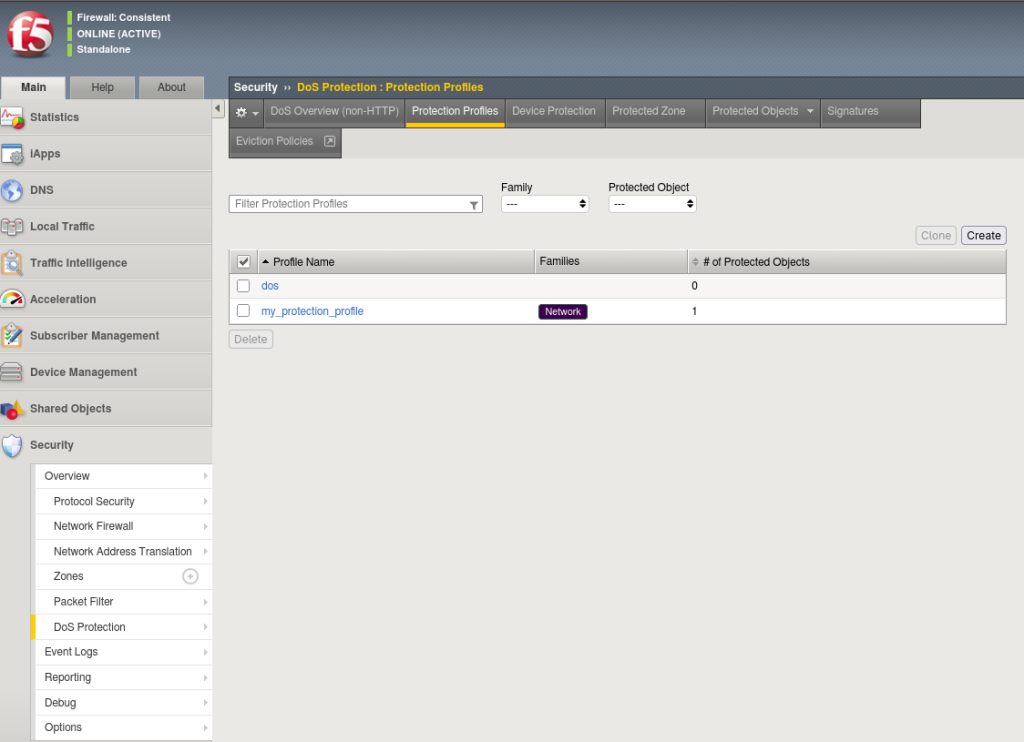
DDoS Protection Profile (Virtual Server)
To protect an application, you must create a DoS Protection Profile.
Navigate to:
Security > DoS Protection > Protection Profiles
From there, create a new profile, assign a name, and select the protocol families (Network, Transport, DNS, SIP, etc.) that should be protected.
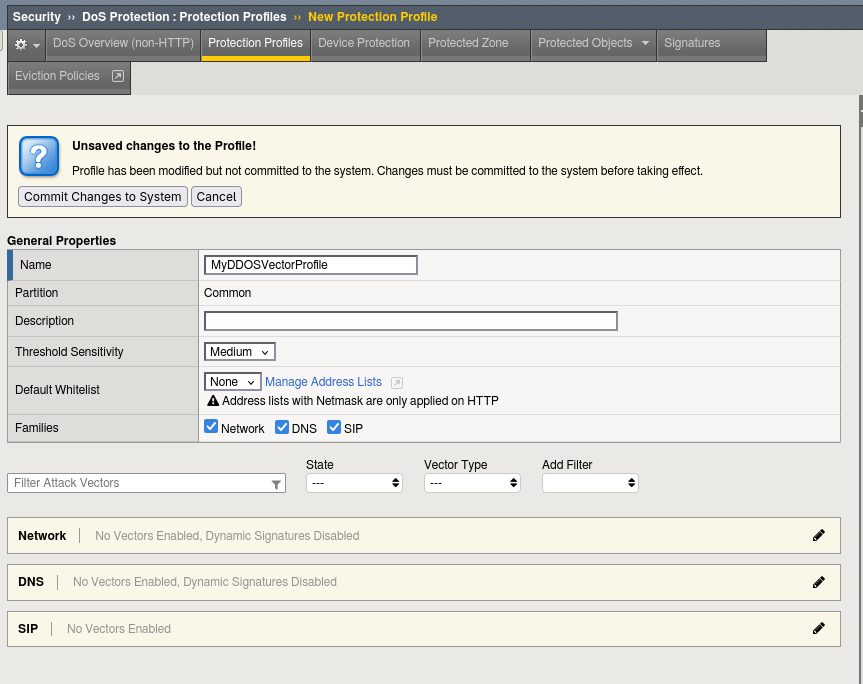
Click on the category name to list all the available vectors, then select the vector you want to activate by setting its State to Mitigate.
The available State options are:
- Disabled: The vector is not monitored and not active.
-
Learn: The system only monitors and learns the packet flow matching the vector. No alerts or mitigation are performed....