Exam Topics
- F5CAB2
- F5CAB2.02
- Explain features of an application delivery controller
- Explain benefits of an application delivery controller
- F5CAB2.02
Introduction
Traditionally, load balancing was a relatively simple task: distribute incoming traffic across multiple servers using predefined algorithms, such as round-robin, least connections, or static weights. While this approach ensures basic availability and scalability, it treats all traffic the same and cannot adapt to the needs of modern applications.
The F5 BIG-IP goes far beyond traditional load balancing. By leveraging its full-proxy architecture, it terminates client connections and establishes separate connections to the backend servers. This design allows the BIG-IP to actively inspect, modify, and control application traffic, rather than simply forwarding it.
Thanks to this architecture, the F5 BIG-IP functions as a modern Application Delivery Controller (ADC). It provides organizations with powerful capabilities, including application optimization, enhanced security, and intelligent traffic control, all from a centralized platform. In other words, the BIG-IP doesn’t just distribute traffic—it ensures that applications are delivered efficiently, securely, and reliably to end users.
What is Load Balancing
At its core, load balancing is the process of distributing incoming network or application traffic across multiple servers to ensure high availability and prevent any single server from being overwhelmed.
Typically, a load balancer sits between the client and the servers and makes a decision about which backend server should handle each incoming request.
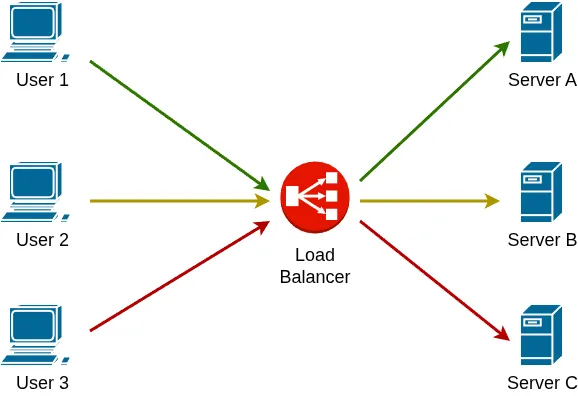
In this example, three clients are redirected to three different servers using the round-robin algorithm, a simple method that distributes requests evenly across all available servers.
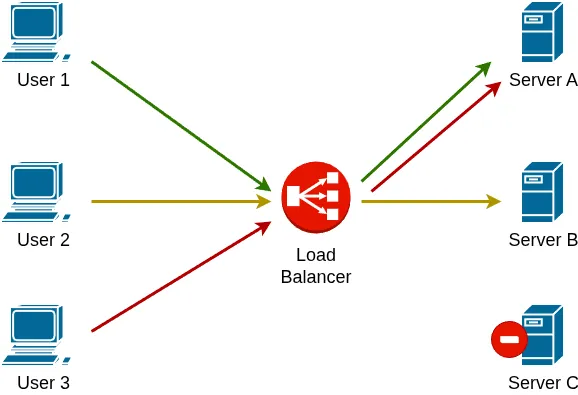
If a backend server becomes unavailable, the load balancer can automatically redirect new incoming requests to a healthy server. By distributing traffic across multiple servers, the load balancer improves overall performance and significantly reduces the risk of service disruption.
These classic load balancers provide basic traffic distribution, but they are often limited in capability. They do not inspect or understand the application layer, cannot modify the content of the data, and therefore cannot perform actions such as security inspection or traffic optimization (for example, compression). In addition, they are unable to apply advanced or dynamic behaviors, such as redirecting traffic based on real-time server load, application state, or administrative conditions.
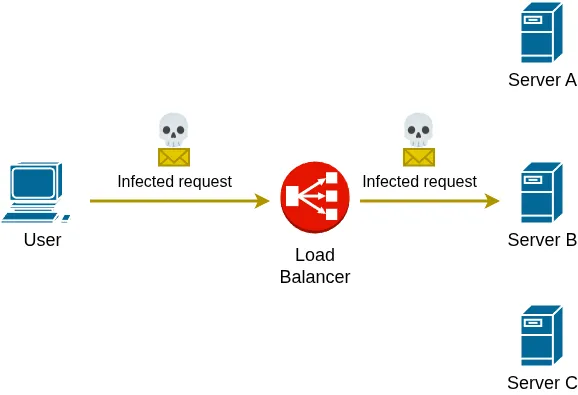
In this example, a malicious request containing a virus, malware, a SQL injection attempt, or other harmful content can still reach the backend server and potentially exploit vulnerabilities. Because traditional load balancers typically do not inspect or analyze application-layer traffic, they are unable to detect or block such threats before they reach the servers.
As a result, traditional load balancing works well for simple use cases but falls short when applications require deeper visibility, control, and intelligence.
This limitation is exactly what the F5 BIG-IP full-proxy architecture solves, enabling modern Application Delivery Control with advanced optimization, security, and intelligent traffic management.
F5 Full Proxy Architecture
The key innovation that sets the F5 BIG-IP apart from traditional load balancers is its full-proxy architecture. Unlike a simple load balancer, which passes traffic directly between clients and servers, a full proxy terminates the client connection and creates a separate connection to the server.
This means that instead of connecting directly to the backend server, the client actually connects to the F5 BIG-IP. The BIG-IP then establishes a separate connection to the backend server on behalf of the client.
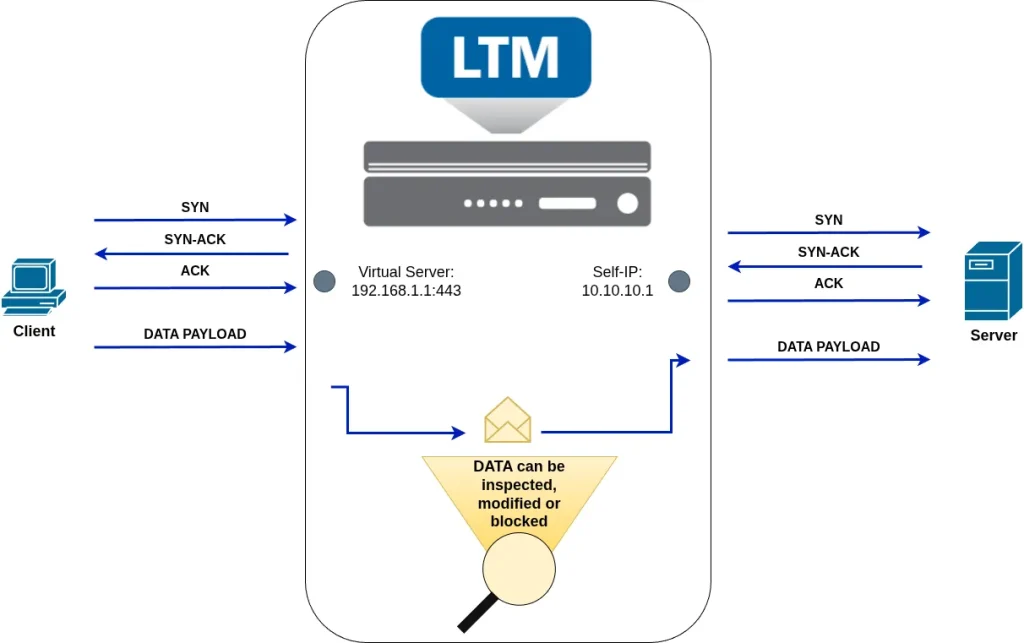
Because it sits between the client and the server, the F5 BIG-IP can inspect, observe, modify, or block traffic as it flows through the system. For example, if a request poses a security threat, such as malware or a SQL injection attempt, the BIG-IP can detect and block the request before it ever reaches the backend server.
This design provides several advantages:
-
Complete visibility: BIG-IP can inspect all traffic, from headers to payloads, for both incoming and outgoing connections
-
Traffic control: Decisions can be made based on application content, not just IP addresses or ports
-
Security enforcement: Malicious traffic can be blocked or modified before it reaches backend servers
-
Optimization opportunities: Connections can be compressed, cached, or optimized to improve performance
By sitting directly in the path of client-server communication, the F5 BIG-IP can act on traffic in ways that traditional load balancers cannot. It can make intelligent routing decisions, enforce application-specific policies, and provide resilience and reliability at the application layer.
In short, the full-proxy architecture transforms the BIG-IP from a simple traffic distributor into a modern Application Delivery Controller, capable of delivering, securing, and optimizing applications in real time.
Modern Application Delivery Controller Capabilities
Now that we have explored the full-proxy architecture, let’s review what the F5 BIG-IP can provide beyond a traditional load balancer.
Optimization
Backend servers do not always implement network or transport optimizations. On the client side, the F5 BIG-IP can apply optimizations when the session is established, without requiring any change on the backend servers.
Common optimizations include:
-
Compression
-
Caching
-
TCP optimization (window scaling, buffer tuning)
These enhancements improve performance and user experience while reducing server load.
Security
As discussed earlier, traditional load balancers do not inspect application traffic. With the F5 BIG-IP, especially when using the ASM (Application Security Manager) module, HTTP requests can be fully inspected to detect malicious content.
The BIG-IP can:
-
Block harmful requests before they reach the server
-
Detect and mitigate bots and DoS attacks
-
Protect applications from common vulnerabilities such as SQL injection and cross-site scripting
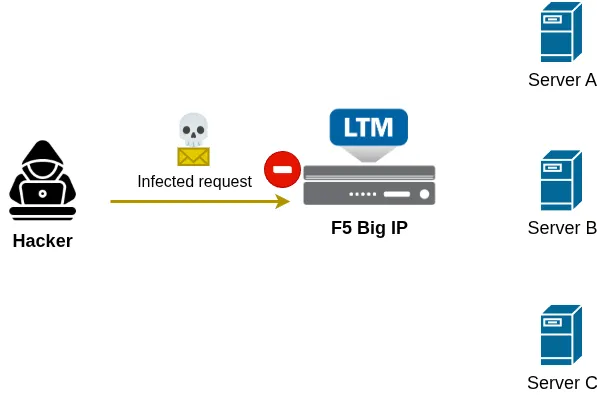
In this example, an attacker sends a malicious request targeting the web server. Because the F5 BIG-IP sits between the client and the servers, it can intercept and analyze the request, detect that it is harmful, and block it before it ever reaches the backend servers.
Layer 7 Load Balancing
Traditional load balancing typically operates at Layer 4, using IP addresses and ports. The F5 BIG-IP introduces Layer 7 load balancing, allowing decisions to be made based on application data.
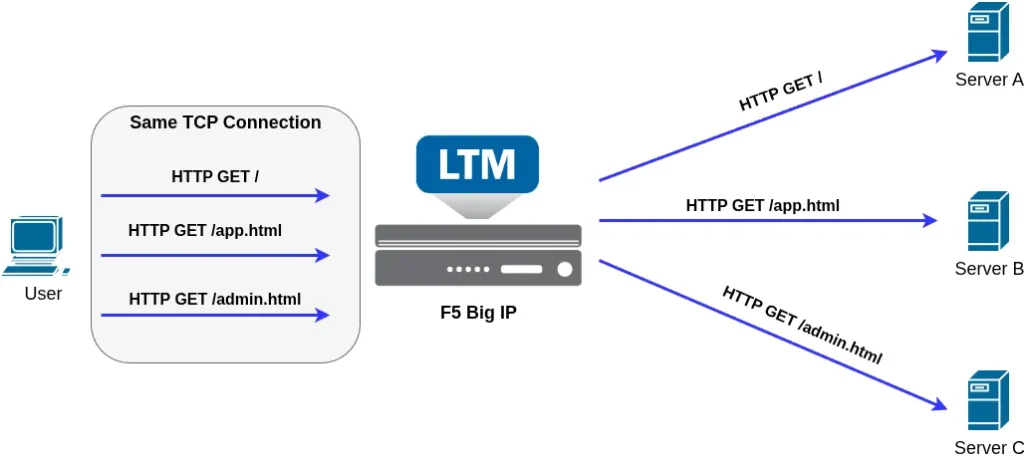
For example, using features such as OneConnect, individual HTTP requests can be distributed across different backend servers, rather than binding an entire TCP connection to a single server.
A traditional load balancer does not distribute traffic at the individual HTTP request level :
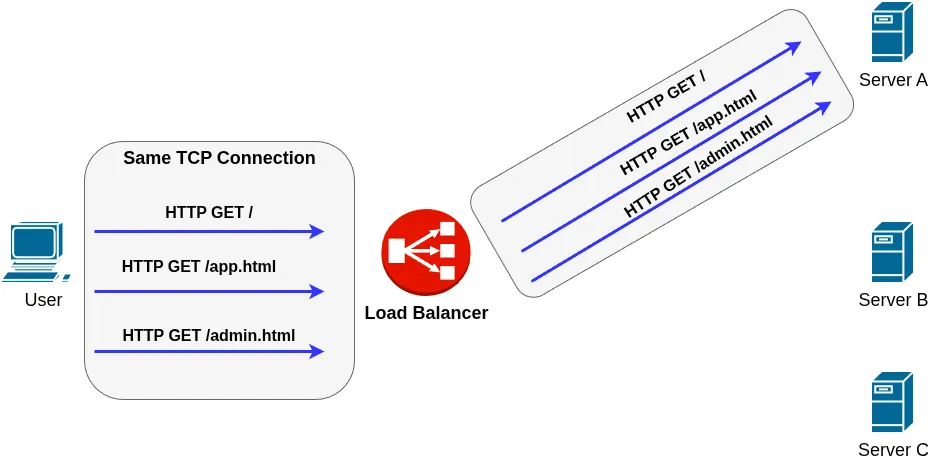
Traffic Modification in Transit
Because the F5 BIG-IP inspects traffic, it can also modify requests and responses in transit. This includes actions such as:
-
Adding or removing HTTP headers
-
Rewriting URLs
-
Masking backend server information
For example, if a backend server exposes headers revealing the web server version, the BIG-IP can remove those headers before sending the response to the client.
SSL Offload
The F5 BIG-IP can terminate SSL/TLS connections on behalf of backend servers. This allows traffic to be encrypted between the client and the BIG-IP while remaining unencrypted on the server side if needed.
SSL offload:
-
Reduces CPU load on backend servers
-
Centralizes certificate and key management
-
Enables security inspection of encrypted traffic
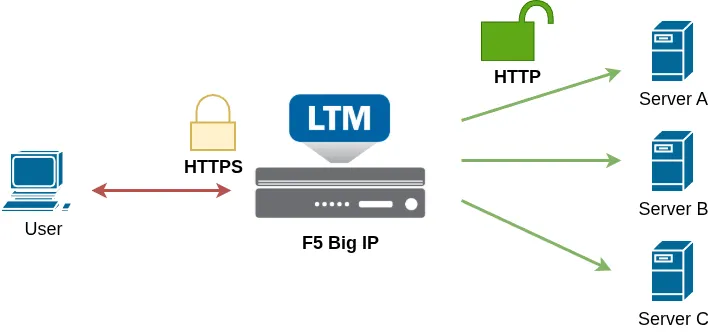
In this example, all certificate management is centralized on the F5 BIG-IP, eliminating the need to renew and manage certificates on each of the three backend servers individually. Since the backend servers now handle only unencrypted HTTP traffic, their CPU usage is reduced, allowing them to focus more resources on application processing rather than encryption tasks.
Authentication
Securing access to applications often requires authentication, which can be difficult to implement on legacy systems. With the APM (Access Policy Manager) module, the F5 BIG-IP can enforce authentication policies before users are allowed to access an application.
This allows:
-
Authentication without modifying the application
-
Integration with external identity providers
-
Centralized access control and policy enforcement
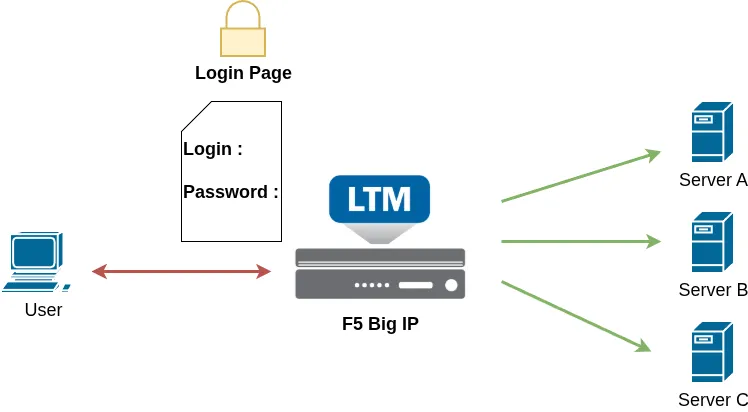
In this example, users are presented with a login page managed by the F5 BIG-IP and must provide valid credentials before being allowed to access the legacy, unsecured backend servers.
Conclusion
Legacy load balancers simply distribute traffic based on IPs and ports, providing basic availability but limited visibility and control. In contrast, modern Application Delivery Controllers like the F5 BIG-IP, with its full-proxy architecture, sit directly in the traffic path and can inspect, modify, or block requests before they reach the backend servers.
This enables precise control over applications, including security enforcement, traffic optimization, Layer 7 routing, SSL offload, and access management—capabilities that go far beyond traditional load balancing and make the BIG-IP a central component of modern application delivery.